Why Cyberattacks on Critical Infrastructure Are Now More Dangerous than Ever
- Ganna Pogrebna
- Jul 14, 2020
- 5 min read
Updated: Nov 27, 2022

If You Can Make It, Cyber Can Break It
With the rise of smart systems, which interfere with many aspects of business, cybersecurity threats are no longer an individual risk or a private sector problem. In the 21st century, adversaries target infrastructure and, especially, critical systems, more and more often. In the realities of working from home, the problem is particularly significant. Imagine an adversarial attack disrupting your water supply, gas systems, power supply, etc. Urban and rural areas are often not prepared to face such cyberattacks. In the pre-COVID world, adversaries could have made significant damage by targeting a large office building. Yet, in the circumstances, when many people are confined to their own homes, the line between attacks on business infrastructure and on city infrastructure becomes very blurred. That means, that in the future cybercriminals and cyberterrorists will target cities more often, with the aim to disrupt the work of businesses as well as damage critical infrastructure.
One of the largest problems with cyberattacks on critical infrastructure is that anybody can do it – the adversary can be a teenager, disgruntled employee, an organized cyberterrorist organization, or even a state-sponsored avdversary. The history of attacks on critical infrastructure proves this point. The first person convicted for causing significant damage to infrastructure and environment through computer hacking was Vitek Boden. Boden was a disgruntled employee of the Maroochy Shire waste treatment plant, who, after leaving the plant on a bad note also failed to secure a job at the Maroochy Shire Council in Queensland, Australia. Seeking revenge, in 2000 Boden broke into the plant’s computer systems and released over 260,000 gallons of raw sewage into the local area damaging environment and causing hundreds of thousands in losses to both the plant and the Council, and requiring almost $700,000 to deal with the aftermaths. Publication of the news also had irreparable psychological effect on the local communities and beyond. This case showed not only that cyber systems can disrupt infrastructure of cities, but also that a lot of damage could be done by a single individual.

Of course, the individual attacks on critical infrastructure are not as frequently observed as attacks originating at a state level or at the level of organized adversarial groups. The motivation for engaging in such attacks also varies from disrupting the systems of an unfriendly state to profit-oriented hacking. Notable cases of critical infrastructure attacks are extremely diverse in nature. For example, Stuxnet was a sophisticated digital warm-like weapon the USA and Israel launched against control systems in Iran in order to sabotage centrifuges at a uranium enrichment plant. Though Stuxnet discovered by the information security community in 2010, the development on it began much earlier - in 2005. The attack on Iran destroyed 1,000 machines and Iran reportedly decommissioned around 20% of its centrifuges in the Natanz plant as a result of it.
In 2015, the German Steel Mill attack disrupted the control systems of a steel mill facility. The attack impacted the IT systems, breaking the mill's crucible, and the steel that was produced during the previous six months (as well as objects and infrastructure which was made of that steel) had to be completely reworked, including buildings that had been constructed using the faulty metal. Ironically, the attack was a simple piece of social engineering as the forensic report revealed that the "adversary used a spear phishing email to gain access to the corporate network and then moved into the plant network." More recently, in March 2018, a well-orchestrated cyberattack on Atlanta in US caused a serious disruption to many city’s functions, some of which were paralysed for many months and led to an estimated damage of $10 million.

What Is the Difference between Cyberterrorists and Cybercriminals?
Cyberterrorists are a subset of cyber adversaries, pursuing non-pecuniary goals. Naturally, cyberterrorist groups may target something or someone for money, yet, money is never the end target for them.
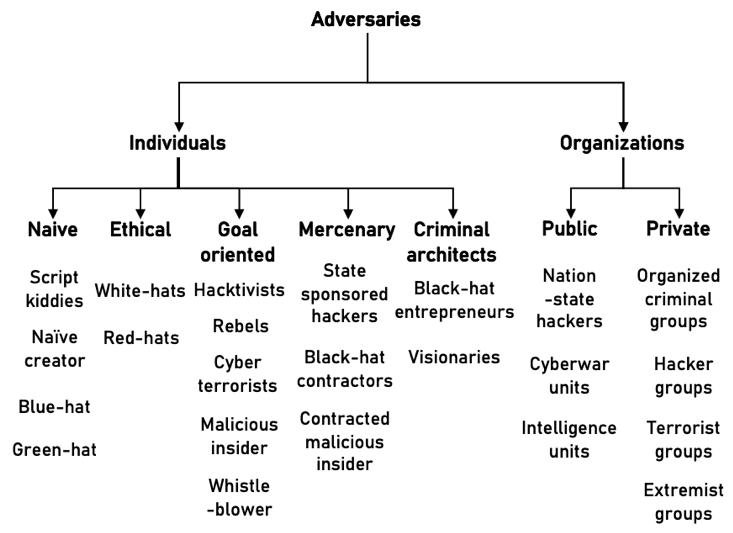
Source: Topology of cyber adversaries as presented in Pogrebna and Skilton (2019), p. 35
If we were to make a more precise distinction between payoff-oriented cybercriminals and cyberterrorists, potential relationships between the two groups often look like an interdependent system. Specifically, cyberterrorists and cyberterrorist groups influence individuals and groups of individuals (e.g., organizations, cities, and even nations) through acts of terror (e.g., by executing attacks on infrastructure, computer systems, networks, etc.). Cybercriminals also impact individuals and groups through various kinds of exploitation activities (theft of money or information, ransomware, blackmail, etc.). Cybercriminals and cybercriminal groups may fund cyberterrorists as cyberterrorist activities may generate additional business opportunities for cybercriminals (e.g., through creating vulnerabilities in computer systems or instigating a panic diversion, which helps cybercriminals attack targets while the targeted security systems or defense mechanisms are trying to deal with the cyberterrorism aftermath). As the same time, it is also possible that cyberterrorists may contract cyber criminals for a range of tasks (e.g., running costs of cybercriminal organizations may be high and cyberterrorists might conspire with for-profit cybercriminals to instigate an attack on a financial institutions with the goal to obtain funds).
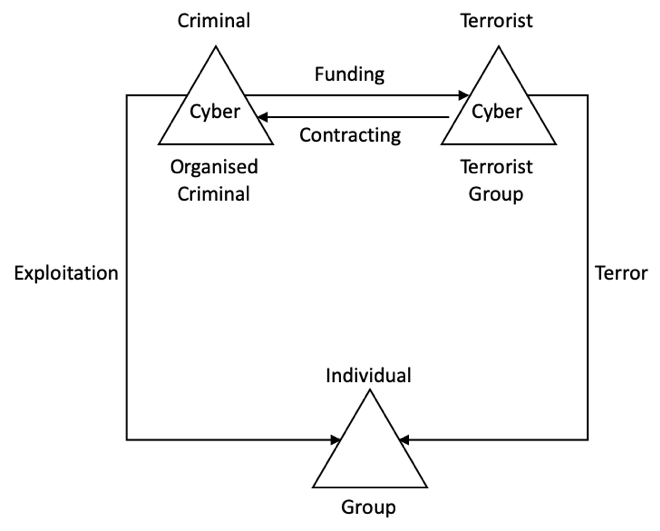
Source: Cybercriminals versus cyberterrorists: relational links and distinctions as presented in Pogrebna (2019)
Takeaways
Considering the variety of adversaries and heterogeneity of their attack tools, what can be done to tackle the problem of critical infrastructure vulnerability? Behavioral segmentation of cyberterrorists is one of many approaches which could be applied to the problem of cyberterrorism risk diagnostics in the absence of detailed and reliable data about cyberterrorists. For example, behavioral segmentation of cyberterrorists could be attained by segmenting cyberterrorists according to their motivation. Cyberterrorists’ motivation may be arbitrary (attacking random targets with the goal of, e.g., increasing population anxiety), emotional (e.g., inspired by retaliation or vengeance), political, religious, moral, ethical, environmental, fundamental, cultural, rational, logical, etc. Obviously, cyberterrorists whose goal is to reach political change will select different targets compared to cyberterrorists whose goal is to establish a different ethical code. These two groups of terrorists will not only select different targets, the severity of their actions will be different dependent on their motivation.
Yet, contemporary risk assessment tools (including those we use in cybersecurity) ignore behavioral components. As a result, the majority of cybersecurity systems concentrate on robustness (i.e., making sure that adversaries do not enter these systems). However, (a) more sophisticated robustness measures tend to attract more knowledgeable and careful adversaries and (b) by ignoring behavioral components we create wasteful and rigid defense systems which often anticipate adversaries in places where attacks are unlikely and, equally, neglect to protect places where attacks are probable. Notably, now we seem to be too preoccupied with many COVID-related tasks and forget how vulnerable our cities are and how easily they may be targeted by cyber adversaries, causing major disruptions to our already significantly changed and not very adaptable "working from home" lifestyles.
#cybersecurity #infrastructure #cyberrisks #cyberthreats #cyberattack #risk #infosec #security #vulnerability #informationsecurity
This post was originally written by Ganna Pogrebna for the CyberBits blog in 2020
Comments