50 Shades of Online Employment Fraud: What We All Need to Know
- Ganna Pogrebna
- May 21, 2020
- 4 min read
Updated: Nov 27, 2022

The beginning of 2020 brought about an unprecedented global challenge - the coronavirus pandemic. Yet, as of today, it is clear that health challenges represent only the tip of the iceberg and the humanity will feel second, third, and forth-order effects for many years to come. One of the major challenges of the current reality is, of course, economic impact of COVID19. And it is already clear that for many people, the main struggle will be to keep their employment, or to find new employment in the corona-aftermath. Naturally, we can also expect that cyber criminals will stream their efforts into designing creative online employment scams.
Why Employment?
I do not know whether you had a chance to follow the recent economy news, so in case you did not, the global employment picture is gloomy. Consider the following facts:
1. The US unemployment is record high with millions of people claiming unemployment benefits weekly. As you can see from the graph below, over the last 8 weeks, between 2.9 and 6.8 million people in the US filed unemployment claims weekly.

Source: BBC based on the data from the US Bureau of Labor Statistics, May 14, 2020
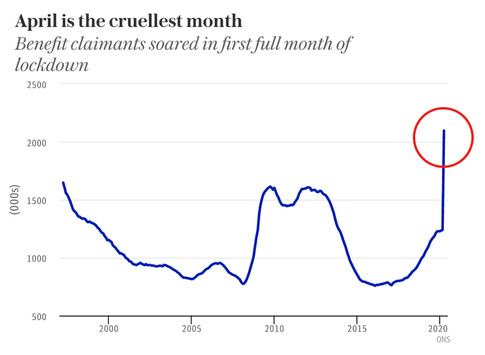
2. In the UK, the claims also increase and the number of vacancies decline, even though the unemployment numbers still have not caught up with the seeming fall in vacancies.
Source: Telegraph Business

Source: BBC based on the data from the Office for National Statistics, UK
3. In Australia over 1.4 million of people are out of work as a result of COVID19

Source: Roy Morgan Research
4. Even though there is some heterogeneity between countries, unemployment rates are expected to increase globally.
Under there circumstances, many people, especially in occupations, where working from home is not an option, start searching for opportunities online; and face many dangers of making their situation even worse as becoming a victim of online employment fraud is now a reality for many.
Online Employment Fraud: Varieties and Examples
A famous American macroeconomist, Hyman Minsky, used to say that the capitalist economic system comes in many varieties. Specifically, he famously argued that "there are as many varieties of capitalism as the Heiz Company has pickles", i.e., 57 varieties. Since, according to Minsky, these different varieties stemmed from different financial arrangements, it would be logical to conjecture that the employment fraud (which also relates to various financial arrangements) should have many shades.

Indeed, this is what we already observe in many employment contexts. So, what are the main variations? Even though within the frame of a short blog we will not be able to discuss all varieties of online employment and employment-related fraud, let us consider 4 most frequent scams:
(i) "Quick and easy earnings" scam: in this case, an unsuspecting victim usually receives an e-mail (it may also be a physical letter or a phone call) telling them about a "quick and easy" way to earn money (e.g., trading, online information sorting, etc.). The scammers then proceed by asking for a payment to send you a "starter kit" or "materials" you would need to complete your training or do your job. Obviously, the scammers never pay the victim the promised salary and disappear with the "starter kit" money. Interestingly, the fraudsters may act through fully legitimate job ad websites.
(ii) The Ponzi scam: a very widespread type of employment fraud, where investors are recruited into a scheme which pays profits to earlier joiners using funds from later joiners. The scammers lead victims to believe that they receive profits from legitimate commercial activity, while in fact they are encouraged to bring in new scheme members and receive profits from the increased network size.
(iii) The money mule scam: another type of scam, where the victims are used as bank account holders and asked to make international transfers of large amounts of money. Sometimes the victims are aware of the fact that their bank account is being used for international transactions. Yet, very often they do not. For example, in one of the recent cyberattacks in the UK, the fraudsters recruited employees to complete simple online research tasks for small remunerations. The victims (employees) had actual online job interviews; were given job tasks, which looked completely legitimate; and even had regular online meetings with their "line managers". On the pay day, these employees receive huge amounts of money on their bank accounts (obviously, the money was stolen). The fraudsters then told the employees that large amounts of money were transferred to them "by mistake" and "the company" would really appreciate if the employee could just keep the amount equal to their salary (+ a small amount of money "compensating the extra labour") and transfer "the remainder" to a different bank account (located abroad). Many of these employees did just that and faced criminal charges for money laundering (as you can probably imagine, not knowing the law is not an excuse the court will accept in cases like these).
(iv) Benefits fraud: with anti-crisis packages and a wide variety of ways in which one can claim governmental aid, especially as a result of the COVID19 outbreak, online scammers may also use sophisticated social engineering techniques to commit or engage others into committing benefits fraud. For example, adversaries may purchase stolen or compromised social security numbers on the Dark Web and make false claims for unemployment funds on victims' behalf.

Take Aways
In the next few months, one of the main cybersecurity threats for individuals, businesses, and countries will arise from online employment fraud. With many people already out of work and many facing financial hardship, online employment scams will come in many shades and varieties. It is, therefore, important to consider how your business and your household will address the new cyber risks, associated with online employment fraud.
#employment #cybercrime #cyberrisks #cyberthreats #datasecurity #cyberattack #onlineemployment #risk #infosec #security #fraud #scam #dataprotection #informationsecurity
This post was originally written by Ganna Pogrebna for the CyberBits blog in 2020



Comments